Basically the problem with http connection is that data is sent and received in plain text. As this data has to pass through a number of routers if somebody want to manipulate it, they can do. Or they can simply do a Man-in-the-middle attack and capture your cookies to hijack your session. This tutorial will show you the ease with which one sitting on your LAN can hijack any of your account if you are using http an connection.
sudo apt-get install dsniff
 In the previous post we have seen how to cut somebody's internet connection on a LAN. There we have poisoned the arp-cache of the victim and gateway with mac addresses which does not exist on the network. But here we will poison it with our mac address. Here we send packets to gateway saying that the victim's mac address is that of ours. And also to the victim saying that the mac address of gateway is that of ours. And now all the packets sent by both the gateway and victim will pass through us. And we can examine these packets by using tcpdump.
In the previous post we have seen how to cut somebody's internet connection on a LAN. There we have poisoned the arp-cache of the victim and gateway with mac addresses which does not exist on the network. But here we will poison it with our mac address. Here we send packets to gateway saying that the victim's mac address is that of ours. And also to the victim saying that the mac address of gateway is that of ours. And now all the packets sent by both the gateway and victim will pass through us. And we can examine these packets by using tcpdump.Before starting the attack you need to take note of a few things, they can be found using the the command ifconfig. Press ctrl+atl+t, this will launch you a terminal there use the command ifconfig
Here you need to note your interface, (mine is 'eth0'). And your network ip, (mine is 192.168.11). These values are used later replace them with yours.
To do a mitm attack you can find all the alive hosts in your network and choose one(or all), here is a small bash script for that using the ping utility
If you dont know how to execute it go here and learn. After executing it you will see the ip addresses of the machines who are currently alive.
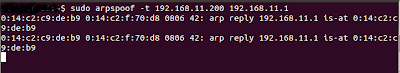
Then you need to poison the victims arp-cache, for that we can use the command sudo arpspoof -t 192.168.11.200 192.168.11.1
Here 192.168.11. is the ip address of my network and 200 is the ip of the host i am going to attack. 192.168.11.1 is the ip of my default gateway, usually it ends with a 1 after your network's ip. After executing this command with proper values you need to open another terminal. And monitor the traffic going through your machine, this can be done using tcpdump. You can always filter out cookies using the grep.
So if i want get the facebook cookies then i will issue the command
sudo tcpdump -i eth0 -A|grep "Cookie: datr="
Since 'datr' is a facebook cookie i will get the output filtered and will only contain facebook cookies. You can drop the datr to get cookies of all the sites or replace it with the cookie of some other site. Note that here eth0 is my interface, you should replace it with yours. So i managed to get my friends cookies.
To use it i copied it and opened firefox and used a firefox-addon tamperdata. Tamperdata can moniter the http traffic between firefox and server and also it can be used to edit cookies on the fly. So i visited www.facebook.com and used tamperdata to replace the cookies with the captured one.
 And on the fly i got his home page, and my friend was amazed and could'nt believe it.
And on the fly i got his home page, and my friend was amazed and could'nt believe it.Here if we want to browse the victims account. We need to edit his cookies for each request. Instead if the attacker used some cookie editor add-on which is easily available online he can really browse it just like his own account. If this sort of mitm attack is combines with a Dos attack, the victim cannot really log out of his machine, he may clear his cookies from the browser thinking it is safe but this makes it worse his account is "permenantly hijacked" as he cannot log out and the attacker can use the same cookies.